Insider Brief
- Google is urging governments and industry to accelerate adoption of post-quantum cryptography, warning that advances in quantum computing could soon undermine the encryption that secures today’s digital systems.
- The company says it has been preparing for a post-quantum world since 2016, rolling out quantum-resistant protections across its infrastructure while aligning its migration plans with NIST standards finalized in 2024.
- Google calls on policymakers to drive society-wide momentum through cloud modernization, global alignment on standards, and closer engagement with quantum experts to avoid security surprises.
One of the global leaders in quantum computing is urging governments, companies and critical infrastructure operators to accelerate preparations for the quantum computing era, warning that today’s encryption systems could be broken sooner than many expect and outlining the company’s own commitments to post-quantum security.
The call to action comes in a new Google blog post by Kent Walker, president of global affairs at Google and Alphabet, and Hartmut Neven, founder and lead of Google Quantum AI. The executives write that quantum computing as both a transformative scientific tool and a looming cybersecurity risk. According to the authors, the same machines expected to drive advances in drug discovery, materials science and energy could also undermine the public-key cryptography that protects financial transactions, private communications and classified data.
“To put that plainly: The encryption currently used to keep your information confidential and secure could easily be broken by a large-scale quantum computer in coming years,” they write.

And while such a cryptographically relevant quantum computer does not yet exist, malicious actors are unlikely to wait. Instead, they are expected to be carrying out “store now, decrypt later” attacks, harvesting encrypted data today in anticipation of future decryption.
Preparation, Not Panic
The post stresses that the response should not be panic, but preparation.
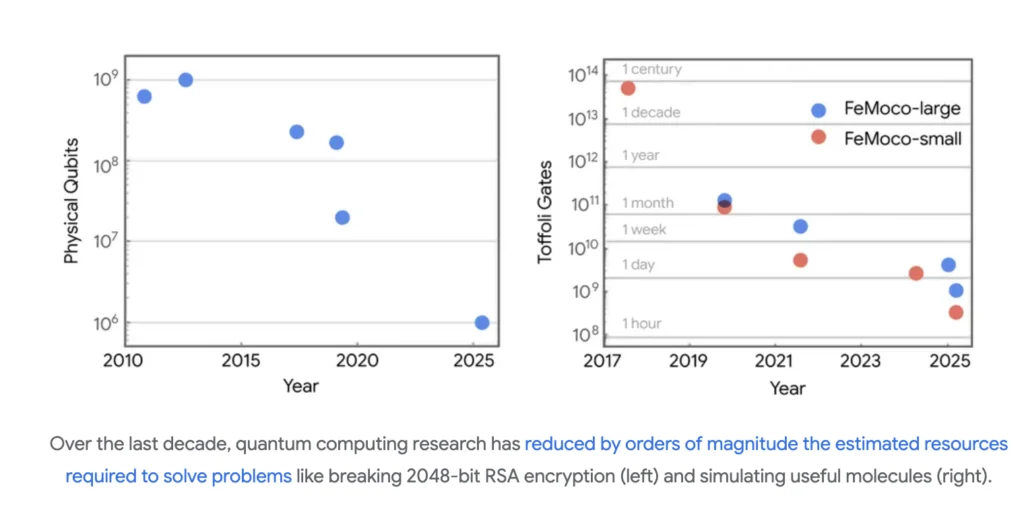
Quantum computing research over the past decade has sharply reduced the estimated resources needed to break widely used encryption schemes such as 2048-bit RSA, while also improving the ability of quantum systems to simulate useful molecules. Walker and Neven write that progress makes it increasingly risky to assume that current timelines for cryptographic transitions can remain static.
The security community has not been idle, according to the post. Cryptographers have developed post-quantum cryptography, or PQC — encryption algorithms designed to withstand attacks from large-scale quantum computers. After a multiyear international review, the National Institute of Standards and Technology announced the first set of PQC standards in 2024, creating a benchmark for governments and industry.
Google suggests it has been preparing for that transition for nearly a decade. According to the post, the company began experimenting with post-quantum cryptography in 2016, rolling out early implementations in products such as Chrome and publishing threat models and technical research. Those efforts are part of a broader strategy focused on what the post describes as “crypto agility,” or the ability to update cryptographic systems without disrupting services.
Google’s Post-Quantum Commitments
The post outlines two areas where Google says it is deepening its commitments.
First, the company plans to continue researching and updating post-quantum timelines, sharing findings where security considerations allow. That work is intended to clarify how advances in quantum hardware and algorithms affect the effort required to break public-key cryptography, including digital signatures and asymmetric encryption. Walker and Neven write that those insights can help sectors such as health care and finance better assess their own migration timelines.
Second, Google says it is on track to complete a post-quantum migration within NIST’s current guidelines and has begun rolling out PQC protections across its internal infrastructure and products. The company says its approach focuses on three areas, specifically, maintaining crypto agility, securing shared digital infrastructure and helping shift the broader ecosystem toward more resilient standards.
The post indicates that the company sees these efforts as investments in the long-term integrity of the digital economy, but also emphasizes that private action alone is not sufficient. Security in the quantum era will require coordinated public- and private-sector engagement, according to the post.
Five Steps for Policymakers
The post offers five recommendations aimed at policymakers.
The first is to drive society-wide momentum, particularly across critical infrastructure. Walker and Neven write that preparation should extend beyond government networks to sectors such as energy, telecommunications and health care, where legacy systems and workforce gaps could slow adoption. Protecting trust infrastructure, including digital certificates, is also highlighted as a priority.
Second, the post urges governments to ensure artificial intelligence systems are built with post-quantum cryptography in mind. As AI becomes more deeply embedded in economic activity its security foundation becomes more critical. PQC should be treated as a prerequisite for durable AI innovation, they add.
Third, Walker and Neven warn against global fragmentation. They write that the NIST standards provide a widely agreed benchmark and that broad adoption would reduce the risk of partial or incompatible solutions that weaken overall security.
Fourth, the post promotes cloud-first modernization as a practical path forward. Transitioning cryptographic systems is a heavy lift and PQC adds urgency to efforts to move away from hard-coded, legacy systems. Cloud platforms allow governments to benefit from ongoing security upgrades rather than bearing the full cost of retrofitting aging infrastructure.
Finally, the post calls on policymakers to engage continuously with technical experts to avoid what it describes as strategic surprise. While no one can predict exactly when a cryptographically relevant quantum computer will arrive, the post cautions against assuming it is always a decade away and recommend ongoing dialogue with research groups and quantum specialists.
The post closes by arguing that quantum computing’s promise and its risks are inseparable. The technology could help solve problems long considered intractable, but only if the transition to quantum-safe security keeps pace.
Walker and Neven write: “Here’s the bottom line: We believe quantum computing can help shape a brighter tomorrow – but we need an all-hands-on-deck approach to make sure the quantum era is defined by breakthroughs, not breakdowns. Working together we can prepare today and promote greater security tomorrow.”
Frequently Asked Questions
Why is Google urging governments to act now on quantum cybersecurity?
Google warns that advances in quantum computing could undermine today’s public-key encryption sooner than many expect, threatening financial transactions, private communications, and classified data. Malicious actors are already expected to be conducting “store now, decrypt later” attacks, harvesting encrypted data today for future decryption.
What is post-quantum cryptography and when were its standards finalized?
Post-quantum cryptography refers to encryption algorithms designed to withstand attacks from large-scale quantum computers. The National Institute of Standards and Technology finalized the first set of PQC standards in 2024 after a multiyear international review.
How long has Google been preparing for a post-quantum world?
Google began experimenting with post-quantum cryptography in 2016, rolling out early implementations in products like Chrome and publishing threat models and technical research. The company says it is now on track to complete a full post-quantum migration within NIST’s current guidelines.
What is “crypto agility” and why does Google emphasize it?
Crypto agility refers to the ability to update cryptographic systems without disrupting services, which Google identifies as a core pillar of its security strategy. It allows organizations to adapt quickly as quantum hardware and algorithms evolve without overhauling entire systems each time.
What are Google’s five recommendations for policymakers?
Google recommends driving society-wide momentum across critical infrastructure, ensuring AI systems are built with PQC in mind, avoiding global fragmentation by adopting NIST standards broadly, prioritizing cloud-first modernization to replace legacy systems, and engaging continuously with technical experts to avoid strategic surprise.
Why does Google warn against assuming a cryptographically relevant quantum computer is always a decade away?
Quantum computing research has already sharply reduced the estimated resources needed to break widely used encryption schemes like 2048-bit RSA, making static timeline assumptions increasingly risky. Google cautions that waiting until such a computer exists before acting leaves too little time for a safe and orderly transition.