Insider Brief
- Meta is initiating a significant transition to post-quantum cryptography (PQC) to bolster security and privacy.
- The company has billions of users on its sites, such as Facebook and Instagram.
- Meta engineers have opted for a hybrid approach, combining classical cryptographic algorithms with PQC algorithms.
Meta is initiating a significant transition to post-quantum cryptography (PQC) to bolster security and privacy for its billions of users. This strategic move, outlined in a recent blog post, offers a glimpse of Meta’s efforts to stay ahead of emerging security threats by adopting cutting-edge cryptographic techniques.
The transition to PQC is not straightforward, according to company engineers.
They write: “Meta’s applications are used by billions of people every day. Given our focus on maintaining user privacy and security, Meta continuously raises its security bar to deploy the most advanced security and cryptographic protection techniques. As part of this continuous effort, we’ve created a workgroup to migrate to PQC, spanning from our internal infrastructure to user-facing apps. This is a highly complex multi-year effort and identifying where to first place PQC protections wasn’t trivial.”

To mitigate the risks associated with migrating to new cryptographic systems, Meta has opted for a hybrid approach, combining classical cryptographic algorithms with PQC algorithms. This hybrid method ensures ongoing protection against current threats while preparing for future quantum-computing risks.
Initially, Meta is focusing on securing components vulnerable to the SNDL attack, particularly those where Meta controls both communication endpoints. The first migration target is Meta’s internal communication traffic, which is crucial and highly sensitive.
Technical Implementation
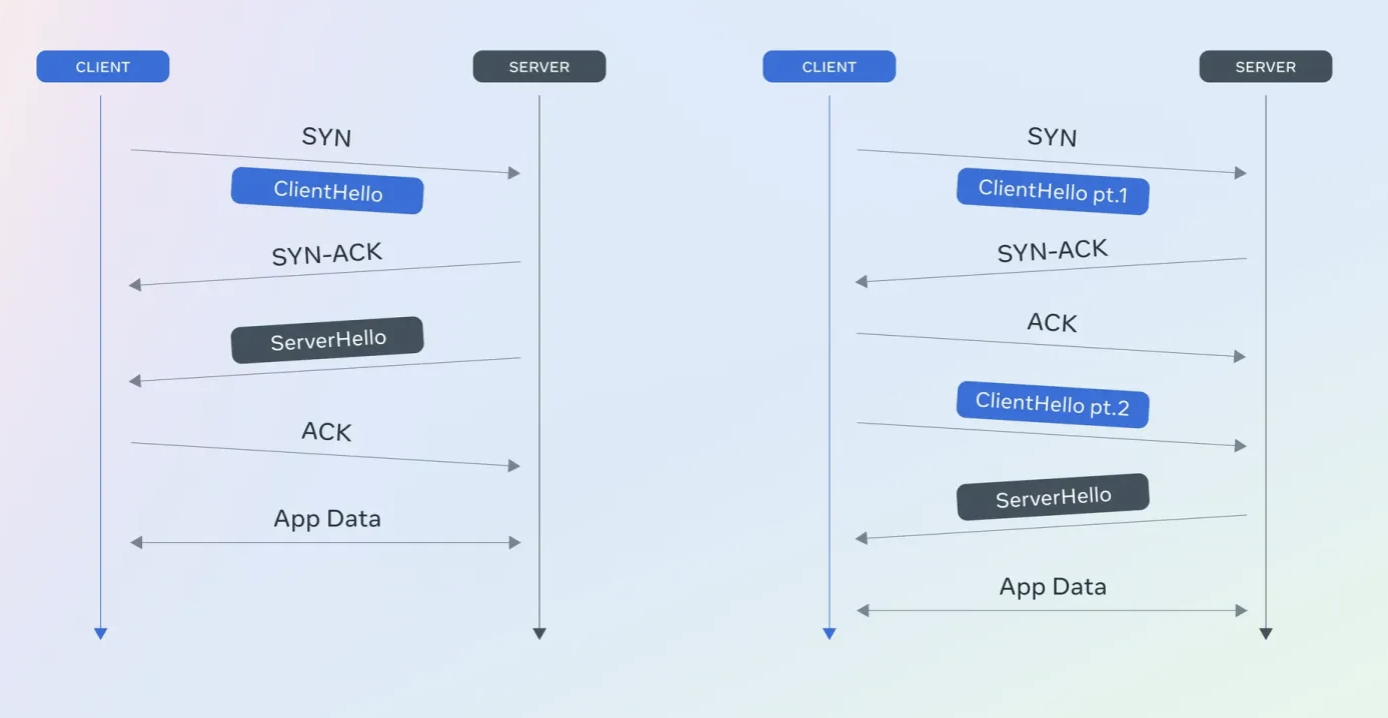
Meta’s deployment leverages a hybrid key exchange method using Kyber and X25519 algorithms. Kyber, the only key encapsulation mechanism selected by National Institute of Standards and Technology — NIST — for standardization, offers varying levels of security and resource requirements. Meta aims to use Kyber768 by default but will deploy Kyber512 in scenarios where performance is a concern, according to the post.
The team writes: “Kyber comes in different parameterizations: Kyber512, Kyber768, and Kyber1024. Larger parameterizations provide stronger security but also require more computational resources and communication bandwidth. We aim to use Kyber768 by default, while using Kyber512 in some cases where larger parameterizations lead to prohibitive performance impact, to accelerate the deployment of PQC hybrid key exchange.”
The implementation is facilitated through Meta’s TLS protocol library, Fizz, known for its high security and performance. Fizz now integrates with liboqs, an open-source library providing post-quantum cryptographic algorithms, and supports hybrid key exchanges.
Challenges and Solutions
The transition is complicated and required several fixes, as detailed in the blog post.
One significant challenge, for example, is the large packet size of Kyber768’s public key share, which exceeds typical TCP segment sizes, impacting TLS handshake efficiency. Meta addressed this by using Kyber512 for certain internal communications to maintain security without compromising performance.
Another challenge involved multithreading issues with liboqs, leading to segmentation faults. Meta resolved this with a fix in the Keccak_Dispatch function, ensuring stable deployment at scale, the team writes.
Meta also encountered problems with cross-domain resumption handshake thrash, where different TLS session scopes using classical and hybrid key exchanges caused inefficiencies. By segregating session scopes, Meta improved the efficiency of key exchanges, despite a minor increase in session ticket storage requirements.
Current Status and Future Plans
Meta has successfully deployed PQC hybrid key exchange for most internal services, protecting against the SNDL threat.
There’s a lot more work to do, the team suggests. The next phase involves extending PQC to external communications, which presents additional challenges such as dependency on browser implementations and increased communication bandwidth.
They write: “Implementing post-quantum hybrid key exchange to external public internet traffic poses several additional challenges, such as dependency on browsers’ TLS implementations and crypto libraries’ PQC readiness, increased communication bandwidth due to larger payloads, and more. We are looking forward to industry standardization and major browser based adoption, and we’ll keep working across Meta to harden our systems as well. We look forward to sharing more as we continue our efforts in this space.”
For a more thorough examination of Meta’s investigation into PQC and their intended solutions, please read the team’s complete blog post.