Insider Brief
- Microsoft has outlined a phased strategy to prepare its services, customers, and partners for the security risks posed by future large-scale quantum computers.
- The company’s Quantum Safe Program aligns with U.S. and international government timelines, targeting full adoption of post-quantum cryptography by 2033 with early adoption beginning in 2029.
- Microsoft is integrating quantum-safe algorithms into foundational libraries, core infrastructure services, and eventually all products, while contributing to global standards and open-source projects.
Microsoft is preparing its cloud, software, and infrastructure for a future where quantum computers could render today’s digital security obsolete. The company outlined a timeline, strategy, and technical measures in a company blog post, warning that organizations need to act now to avoid disruption when large-scale quantum computing arrives.
The team added that their Quantum Safe Program aligns with current efforts to prepare society for a post-quantum future.
Quantum computers are still in early stages, but if scaled, they could solve certain problems beyond the reach of today’s fastest supercomputers. That power comes with a downside: they could break the mathematical locks that secure online transactions, encrypted communications, and digital identities. Public-key cryptography — the system that allows users to verify websites, sign financial records, and authenticate logins — would be vulnerable.

The team noted in the blog that even though large-scale quantum machines are not yet available, adversaries could exploit a tactic known as “harvest now, decrypt later.” In this scenario, encrypted data is stored today with the intent of unlocking it once quantum capabilities catch up. Microsoft’s view is that this raises the urgency for governments, businesses, and technology providers to begin migrating to what is known as post-quantum cryptography, or PQC.
Migration, Not a Switch
The company emphasized that the transition to quantum-safe systems will not be a sudden cutover. Instead, it is a multi-year transformation requiring coordinated planning, standards alignment, and technical changes across software and hardware. Microsoft framed it as both a risk and an opportunity: organizations can use the shift to replace outdated systems, adopt modern cryptographic libraries, and embrace “crypto-agility,” the ability to switch algorithms more easily as threats evolve.
Microsoft’s work in this area stretches back more than a decade. According to the blog, the company began research into post-quantum algorithms in 2014 and later carried out experiments in cryptanalysis to test when existing algorithms might break. In 2019, its researchers tested an experimental quantum-safe virtual private network, linking its Redmond campus with a datacenter submerged off Scotland as part of Project Natick.
Since then, Microsoft has played a role in developing algorithms, joining standards groups, and contributing to open-source efforts. It has worked with the National Institute of Standards and Technology’s (NIST) call for proposals to identify viable post-quantum cryptographic methods. Its FrodoKEM algorithm, developed with academic partners, is under consideration for international adoption as an ISO standard.
Microsoft also contributed to the Open Quantum Safe project, which builds tools for integrating post-quantum algorithms into internet protocols. In 2024, the company announced an open-source hardware accelerator called Adams Bridge, built to handle post-quantum cryptographic workloads and integrated into the Open Compute Project’s Caliptra 2.0 platform.
Building a Quantum Safe Program
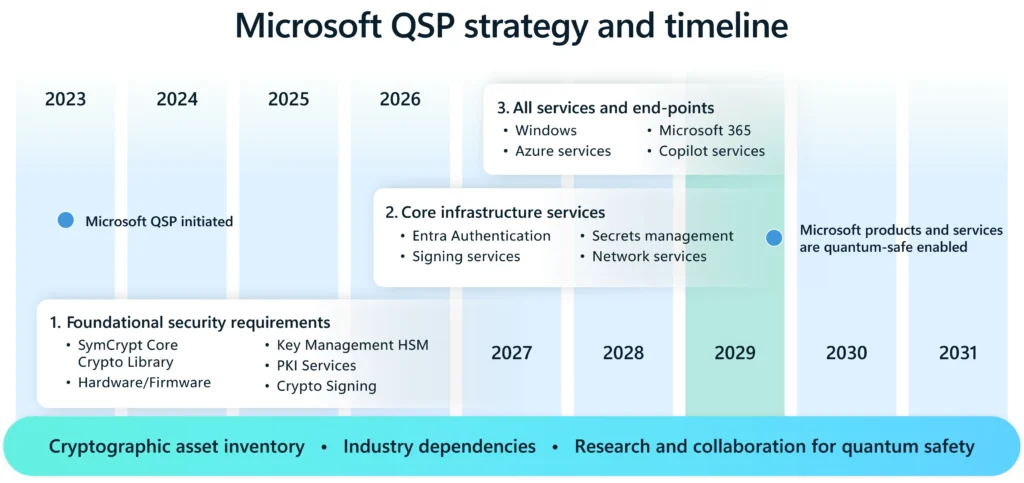
The blog described how Microsoft formalized its efforts in 2023 with the creation of the Quantum Safe Program, or QSP. The program consolidates research, product development, and standards work across the company and aims to protect both Microsoft’s infrastructure and that of its customers and partners.
The program is designed around three priorities: first, to make Microsoft’s own systems quantum safe; second, to help customers and partners adopt post-quantum tools; and third, to promote global standards and research. It is governed by a leadership team spanning business, engineering, and research groups.
One of the first steps was an enterprise-wide inventory of cryptographic assets, a process to identify where risks exist and which systems will need priority upgrades. That assessment fed into Microsoft’s phased roadmap.
The Phased Transition
Microsoft’s transition plan has three broad phases. The first centers on foundational security components, such as SymCrypt, the cryptographic library underlying Windows, Azure and Microsoft 365. The company has integrated post-quantum algorithms, including ML-KEM and ML-DSA, into SymCrypt, making them accessible to developers through Windows’ cryptography APIs and certificate services. These changes are already available to Windows Insiders and Linux environments.
The second phase focuses on core infrastructure services. This includes identity and authentication systems such as Entra, as well as key management and signing services. Microsoft’s view is that securing these elements first will create a strong base for protecting sensitive workloads.
The final phase extends to all services and endpoints — Windows operating systems, Azure cloud services, Microsoft 365 productivity applications, data platforms, and AI services. By embedding quantum-safe algorithms broadly, Microsoft aims to secure its ecosystem end-to-end.
The company said its roadmap aligns with guidance from U.S. agencies including NIST, the Cybersecurity and Infrastructure Security Agency (CISA), and the National Security Agency (NSA). It also monitors efforts in Europe, Japan, Canada, Australia and the UK. Microsoft’s plan targets full transition by 2033, two years ahead of the 2035 deadlines set by many governments. Early adoption is expected by 2029, with quantum-safe systems gradually becoming the default.
Internationally, the effort to standardize post-quantum cryptography is well underway. NIST has been evaluating candidate algorithms since 2017, and draft standards are emerging for protocols like Transport Layer Security (TLS). Microsoft has already enabled hybrid key exchange in OpenSSL through its SymCrypt integration, in line with current IETF drafts.
Next Steps
The company underscored that the challenge is not only technical but also organizational. Legacy systems, fragmented standards, and the scale of global IT infrastructure make migration complex. At the same time, the risks of delay are high. Sensitive government records, financial transactions, and personal communications encrypted today could be vulnerable to decryption in the future.
Microsoft argued in the blog that preparation must begin immediately to avoid a last-minute scramble. The company framed its work not as a defensive posture but as part of its broader investment in the quantum future, which includes building its own quantum processors and error-correcting codes alongside developing defensive cryptography.
In prior updates, Microsoft has offered practical steps for organizations to start their transition. These include conducting cryptographic inventories, testing post-quantum algorithms in pilot projects, and engaging with standards groups. The blog indicated that further updates will continue to share lessons learned from Microsoft’s deployments and experiments.
The shift to quantum-safe cryptography is one of the largest security overhauls in decades. As with the move to the internet and the adoption of cloud services, it will take years and require coordination across governments, industries, and vendors. Microsoft’s position is that those who start planning now will be best positioned to withstand the disruptive power of quantum computing when it arrives.