This article covers an Introduction to Post Quantum Cryptography, why it’s important and organizations should act now, the different approaches to Post Quantum Cryptography, some key companies and case studies. Research and composition was undertaken by Elias Lehman, Quantum Computing at Berkeley and TQI analyst and Matt Swayne, TQI editor and analyst.
Introduction to Post Quantum Cryptography (PQC)
In today’s interconnected world, globalization of commerce, culture, and communication is inevitable. Predicting the accelerated growth of the internet, engineers and cryptographists implemented security systems to protect the information we exchange. This system is what we rely on to send emails, texts, browse the internet, send virtual signatures, log into our banking platforms, and much more. However, the increasing complexity of our digital lives and advancement in quantum technology is raising concerns as quantum computers possess the potential to break modern encryption techniques, and cyber security risks are a growing concern for companies.
In this article, we will review the implication of quantum in the field of cybersecurity and explore why post quantum security is so important. Although expert predictions on when quantum computers will be robust enough to crack current cryptographic schemes range from tomorrow to decades, we will identify a critical reason why organizations should prepare for this eventuality now. Finally, we will offer an overview of the current post quantum security market and provide some case studies of companies that are working on solutions to the quantum threat.
Why is Quantum Security important?
The power of quantum computers derives from superposition and entanglement. The ability to hold quantum bits of information – or qubits – in a combination, or superposition, of various states at once, compared to classical computers with bits that can either represent a 1 or a 0. Quantum entanglement – the quantum mechanical phenomena in which physically separated particles can still share quantum states – allows a quantum computer that can hold this delicate state of entanglement to exponentially boost its computational power for each entangled qubit.

While the technology’s ability to deliver solutions to some of the most pressing scientific and societal challenges is driving billions of dollars in investment and global scientific collaborations, experts also warn that it could leave most of the protocols used to protect data and privacy vulnerable to future quantum computers.
At the heart of the concern about data privacy and security in the post-quantum era is Shor’s Algorithm. Developed by mathematician Peter Shor in 1994, the algorithm can find integers of prime numbers when run on a quantum computer of sufficient power. The complexity of prime number factorization is precisely the method that current public key (asymmetric) encryption schemes, such as RSA and elliptic curve cryptography (ECC), are built on to secure data.
Why act now?
Cybersecurity specialists fear that criminals anticipate the application of quantum computers to break modern encryption and have begun collecting encrypted information which is vulnerable in the future. Although quantum-advantage in cryptography is thought to be a decade or more away, the ongoing breakthroughs in quantum computer capabilities is causing cybersecurity experts to worry that we are already seeing “steal now, decrypt later” attacks.
In January 2022 the Biden administration required all US government agencies to produce a response plan within the next 6 months. In April, US Congressmen introduced the Quantum Computing Cybersecurity Preparedness Act, requiring US Federal agencies to start the prioritization process for PQC migration within one year following the establishment of standard protocols. This is estimated to be 2025-26. On the other hand, the European Commission enacted The European Quantum Communications Infrastructure (EuroQCI) Initiative in 2019, aiming to implement a quantum-secure internet system in Europe by 2027 using Quantum Key Distribution (QKD).
This article focuses on Post Quantum Cryptography (PQC) which addresses the challenges posed by future quantum computers without requiring the significant engineering or technical breakthroughs required in Quantum Encryption (QE).
Analysing the different approaches to Post Quantum Cryptography (PQC)
There are several organizations working on analysing PQC candidates (for example CACR in China) but most market stakeholders are focused on tracking efforts being pursued in the USA. The National Institute of Standards and Technology (NIST) is a USA research facility dedicated to setting regulations and analytical metrics for a large span of industrial instruments, particularly in measurements, communications, and security. Predating the Biden Administration’s emphasis on QIS, NIST began a 7-year program dedicated to determining one or more qualified candidates for national standards in PQC, which is likely to become a reference when standards are implemented internationally. Initial results were announced 5 July, 2022, long before a successful QE system has been implemented nationwide.
Figure X – NIST Candidate Process
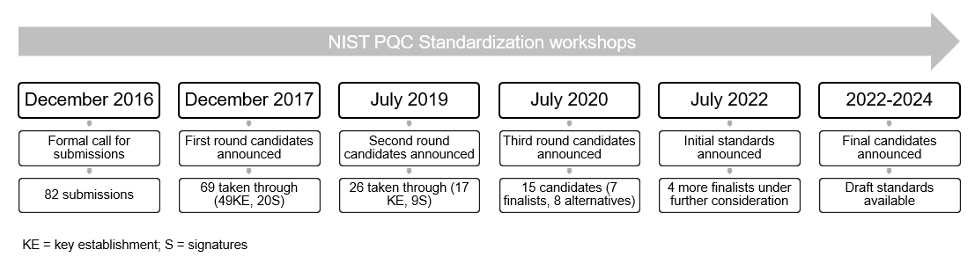
NIST candidates are judged on several criteria which need to be balanced for an effective protocol.
Through two rounds of this evaluation process, NIST selected seven finalists for standardization, and eight alternate candidates for further study and to compete in a final fourth round for possible standardization. In the third and latest round, NIST selected three finalists and one alternate for standardization. The resulting algorithms are separated into two encryption technologies, Public-Key Encryption and Digital Signatures, and are subdivided into their mathematical encryption family below.
| Public-Key (General) Encryption | Algorithm Family |
| CRYSTALS-KYBER | Lattice |
| Digital Signatures | Algorithm Family |
| CRYSTALS-DILITHIUM | Lattice |
| FALCON | Lattice |
| SPHINCS+ |
Hash |
Of the 4 algorithms, 3 are of the lattice family, a method which leverages either the difficult factorization of polynomials or uncovering a matrix scattered with errors. Lattice algorithms are considered great candidates for general purpose application as they can be used for both encryption and verification.
The other algorithms come from high-entropy hash functions. Secure hashing algorithms, such as SPHINCS+, require large keys and are significantly slower to cipher but it makes for a reliable backup to the lattice methods. Four remaining alternate algorithms are not out of the picture, either (though we are seeing evidence of some already being broken). Some are very powerful yet so novel that they require further analysis to qualify for standardization.
NIST’s Final Candidates
In August 2023, NIST selected four algorithms that it will standardize as a result of this Post-Quantum Cryptography (PQC) Standardization Process. They include CRYSTALS–KYBER, along with three digital signature schemes: CRYSTALS–Dilithium, FALCON, and SPHINCS+.
The four algorithms were the culmination of this meticulous multi-year selection process for selecting these algorithms that starting when NIST issued a public call for submissions to the PQC Standardization Process in December 2016 that came about as the institute recognized the disruptive potential of quantum computing development and deployment. The institute suggests that these four algorithms will serve as global benchmarks for data privacy and security throughout the quantum era.
Case Studies
This section provides case studies on the various approaches being taken to quantum security. This is by no means an exhaustive list; indeed, our quantum security database covers over 60 companies across the wider quantum security market, which includes players working on QKD, Quantum Random Number Generators (QRNGs), PQC and the hardware required across the board.
Figure X – Quantum Security Landscape

Company comparison
Company profiles
| Arqit | Qrypt | Quantropi | PQShield | |
|---|---|---|---|---|
| HQ | London, UK | New York, USA | Ottawa, Canada | Oxford, UK |
| CEO | David Williams | Kevin Chalker | James Nguyen | Ali El Kaafarani |
| Source of entropy | Pseudo-QRNG | QRNG from national labs | QRNG and Pseudo-QRNG | Internal RNG and hash |
| Encryption protocol | Uses AES256 Symmetric Algorithm in hand with zero-trust architecture. Once developed, satellite QKD protocol will provide scalability for cloud use-cases. |
Uses patented BLAST protocol to generates symmetric keys or one-time pads at end points eliminating key transmission risk. Uses existing standard encryption libraries or solutions to encrypt. |
Works with NIST candidates, as well as proprietary patented Multivariate Polynomial Public Key (MPPK) – allows for quantum-secure key exchange without drastically increasing key size. | Works with NIST standard FALCON and third-round candidate NTRU to secure software products. Hardware generates and stores keys to perform mobile encryption and decryption. |
| Data Management | Secure keys kept in international data centres |
Existing key management solutions can be leveraged |
Operates live over existing optical infrastructure | Keys are stored locally on PQS hardware product |
| Target markets | Industry IoT, Wireless Carriers, Financial Institutions, Governing Bodies | Application Developers, Cybersecurity Software Companies | Blockchain, IoT, Application Developers | Critical Infrastructure, IoT, OEM |
| Known example customers / partnerships | UK Government, Northrop Grumman, Verizon | Gigstreem, Fornetix, Vaultree, Megaport | Deutsch Telekom, Torus | Microchip Technology, Collins Aerospace |
| Other differentiators | Distributed nodes, in hand with clustered device families allow for efficient privatized networks | Simple SDK and API for ease-of-use implementation within individual products | Suite of cybersecurity applications covering PQC symmetric and asymmetric encryption | Multifaceted solutions which span various industrial implementation techniques
|
Technology deep dives
Quantropi
Quantropi is looking to offer symmetric encryption that’s faster than AES-256, as well as providing strong random numbers across networks that can’t be reached by traditional QKD. Its core product is the QiSpace platform which offers asymmetric and symmetric encryption/decryption and Entropy as a Service (EaaS), through its services MASQ, QEEP, and SEQUR, respectively.
Entropy comes from quantum circuits comprised of a series of permutation gates. The circuit can be run on a quantum computer or simulator to provide either QRNs or pseudo-QRNs. This supports Quantropi’s Quantum Permutation Pad (QPP) technology onto which the SEQUR EaaS products are built.
The business uses both its proprietary PQC algorithm as well as NIST candidates. The logic is that whilst NIST will provide users with a reliable standard, it may be that the algorithms chosen may have digital signatures too long for certain commercial cases. As a solution, Quantropi claims a patented Multivariate Polynomial Public Key (MPPK) algorithm that ensures short enough keys for many-signature applications, such as Blockchain.
The business’s key distribution method is closely related to QKD, but does not require new distribution technology such as special optical fibers or data storage. Called Coherent-based Two-Field (CTF) QKD, the technology is a novel optical modulation technique that is compatible with today’s optical fiber infrastructure.
Quantropi’s solutions are targeted towards to the live transmission of data, requiring minimum new infrastructure. They assume the client’s data storage methods are self-secure.
Qrypt
Qrypt enables the independent generation of symmetric keys or one-time pads at multiple end-points without any distance constraints or need for hardware. As cryptographically relevant quantum computers will break RSA and ECC encryption, and NIST PQC algorithms are new and have yet to show resilience over time, Qrypt’s approach focuses on eliminating key transmission and using one-time pad encryption for long-term security. This business already provides a commercial Entropy as a Service (EaaS) offering
Qrypt’s solutions leverage their own Quantum Entropy Service (EaaS offering). The QRNGs for this service are manufactured in the United States and developed in partnership with the Department of Energy’s Oak Ridge National Laboratory (ORNL).
Qrypt Quantum Key Generation is the heart of their quantum security offerings. True quantum random numbers are the resource to generate keys or one-time pads. Once generated a recipe is then created that includes server and key generation parameters. This short-term recipe is then shared with recipients. This recipe is sent over any channel that can maintain data security for at least an hour. RSA, ECC, and NIST PQC all meet this requirement. Random number pools used to generate the keys are shredded each hour.
Long-term and quantum security is achieved as (a) encryption keys are not transmitted and cannot be captured, or (b) one-time pads are generated, and data encrypted with onetime pads is information-theoretically secure, i.e., mathematically impossible to be decrypted even by quantum computers. Even if a future technique is invented to break encryption, previously transmitted data isn’t at risk as keys were not harvested; you update recipe transmission to the latest encryption standards.
Qrypt’s approach is post-quantum cryptographically secure and can be integrated into existing infrastructures without majorly replacing existing algorithms. To secure key transmission now you can either generate keys or leverage a quantum-secure (one-time pad encrypted) tunnel.
ArQit
In contrast to the other companies mentioned ArQit is publicly traded and has an approach that combines both a quantum entropy source and symmetric encryption. Currently, the business provides SaaS Quantum encryption solutions that run on their QuantumCloud service.
Random numbers from a pseudo-quantum generator act as the seed for AES-256 keys. The company aspires to soon generate keys on satellites for a distribution system similar to QKD.
The business’s current solution is initialized through a provisional process called Autonomous Trustless Keyfill (ATK). A device sends an identifier to the QuantumCloud, which in return produces an authentication key compatible with only the device and the cloud service. This shared key is used throughout symmetric encryption process.
Provisioned devices are then enrolled in ArQit’s Distributed Symmetric Communication Cryptogrpahy (DSCC) system. As a centralized platform, DSCC allows for internal negotiation of keys between devices and data centers and minimizes the number of certifications required between a device and the cloud. Once in the system, the QuantumCloud can recognize interactions between itself and a particular device through a unique identifier, giving administrators provisional abilities over the permissions of every device.
Symmetric key data is stored in global data-centres and other cloud providers which act as nodes for secure key exchange. The network architecture of ArQit’s cloud solution has such similarity to today’s internet protocol that they claim their approach is supported by standard TLS1.3.
PQShield
PQShield started by focusing on Critical Infrastructure, OEM and IoT markets, giving their focus to physical devices but appears to be expanding out to providing a full cryptographic development toolkit for mobile and server technologies, as well as messaging platforms and apps.
We understand the business has not yet integrated a quantum source of entropy (but expect it is something they are working on and is common to many peers).*Update: PQShield confirms to TQI that PQShield has integrated entropy to its hardware solutions.*
The company emphasizes their work on microcontrollers, lightweight hardware which they term post-quantum System on Chip (PQSoQ), for applications in IoT and OEM. PQSoC supports internal random-number generation in addition to the standard RISC-V and peripheral user interface.
What makes their hardware unique is a custom PQC co-processor, allowing for IoT developer to implement their own protocol using PQSLIB, a library of PQC primitives including NIST standards and alternatives. The PQC-compatible processer and random number generator allows for local secret key generation, encryption, decryption, authentication and signing, making it suitable for secure elements, smart cards, and embedded security chips.
PQShield also offers PQSDK Crypto, a library for applying NIST standard primitive FALCON and third-round candidate NTRU to software applications. The SDK combines the PQC algorithm with standard internet certification protocol to provide secure digital signatures, and connection of these signatures to ensure network security.
Other than storing secret keys on their chips, PQShield does not offer a compelling data storage system as far as we are aware. The business is targeted towards data in motion such as communication applications and live signatures. Their primary service is allowing engineers custom encryption, regardless of implementation technique.
Conclusions
Today’s citizens, governments, private industry and governments benefit from the many services technologies provide. These services are primary based on dated security protocols, which increasingly look vulnerable. This article demonstrates the challenges presented by a future powerful quantum computer. We have also exhibited the approaches that are being worked on to achieve security from this threat using PQC.
In this case study approach, we have identified which PQC companies are best applicable for different use cases. An organization in search of developing a lightweight security system may look to Quantropi to provide support. For a company developing hardware or IoT, PQShield may be a great candidate.
We recommend corporates and governments engage early with quantum security providers to assess the robustness of their product offering and the ease with which they facilitate the implementation of a quantum secure environment. Important factors to consider are (i) the quality of the technology and the team; (ii) the speed and support of an implementation; (iii) the long-term flexibility provided by the implementation (i.e., crypto agility) and (iv) the robustness of the solution (i.e., does it address data in motion and data at rest).
If you found this article to be informative, you can explore more current quantum news here, exclusives, interviews, and podcasts.