Insider Brief
- A Federal Reserve study warns that quantum computers could one day decrypt Bitcoin’s historical transactions, exposing private data recorded under current encryption standards.
- The report finds that “harvest now, decrypt later” attacks are an active threat, as adversaries can collect encrypted blockchain data today and unlock it once quantum computers become powerful enough.
- While post-quantum cryptography may protect future transactions, the study concludes that no existing method can retroactively safeguard data already stored on public distributed ledgers.
A new Federal Reserve study warns that quantum computers could one day unlock the private history of Bitcoin and other blockchain networks, exposing transaction data once thought to be forever secure. The report, titled “Harvest Now, Decrypt Later,” says the risk is not distant, — it is already active today as attackers quietly collect encrypted data, waiting for the moment when future quantum machines can break it.
The analysis, published by the Federal Reserve Board and the Federal Reserve Bank of Chicago, centers on a threat researchers call “harvest now, decrypt later,” or HNDL. It’s a simple concept, but could have far-reaching effects. HNDL simply means that adversaries can download or intercept encrypted information today, store it, and later use a sufficiently powerful quantum computer to reveal its contents.
The study finds that distributed ledgers like Bitcoin are particularly vulnerable because their entire transaction histories are public, permanent, and based on cryptographic methods that quantum computers are expected to defeat.

Quantum Risks
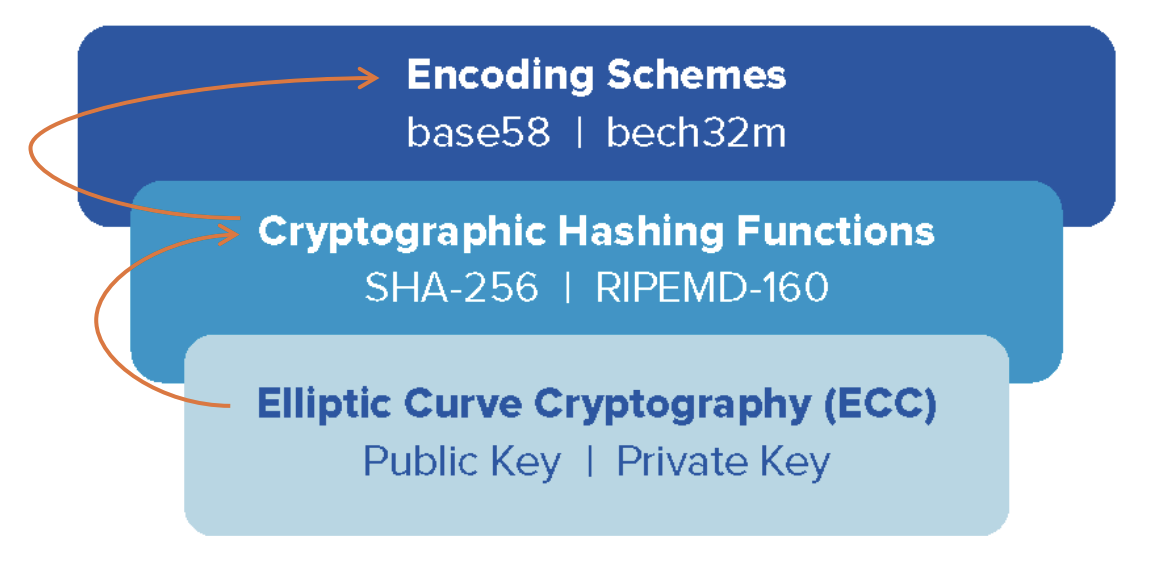
Quantum computers operate using quantum bits, or qubits, which can exist in multiple probabilistic states simultaneously, a property known as superposition. This allows them to theoretically perform many calculations at once, potentially solving problems that would take classical computers thousands of years. One of those problems involves factoring large numbers, which is the foundation of many modern encryption systems. The report from the Federal Reserve Board explains that public-key systems such as RSA and Elliptic Curve Cryptography (ECC), which secure most internet traffic and blockchains, rely on the difficulty of this mathematical task. In 1994, mathematician Peter Shor showed that a quantum algorithm could make short work of such problems, breaking these systems in minutes once enough stable qubits are available.
That possibility has transformed what was once an academic idea into a looming cybersecurity issue. According to the report, when so-called “Q-Day” arrives—the moment quantum computers can routinely break existing encryption—data secured by traditional cryptography could be instantly compromised. But the authors note that HNDL means the real risk starts long before Q-Day. Anyone who has already copied a blockchain ledger or intercepted encrypted traffic could later decrypt it, turning past communications, financial transactions, and private records into readable text.
The analysts of the study, Jillian Mascelli and Megan Rodden, write: “Increasingly fault tolerant and stable quantum computers will threaten existing public-key cryptography and may prompt legacy system maintainers to update their traditional cryptography to post-quantum cryptography (PQC) in response. While this paradigm shift may present future operational and security risks, we highlight a present, active, and in some circumstances unavoidable data privacy risk posed by future-state quantum computers. This risk could be exploited through the actions known as “harvest now decrypt later” or HNDL.”
Bitcoin as a Case Study
The researchers rely on Bitcoin as a model for understanding how HNDL could affect decentralized financial networks. Bitcoin was introduced in 2009 by a person or group using the name Satoshi Nakamoto as the first decentralized digital currency, designed to allow peer-to-peer payments without banks or intermediaries. Its underlying technology, the blockchain, records all transactions on a public ledger maintained collectively by a network of computers rather than a central authority.
This distributed ledger recorded every transaction since its creation in 2009. Anyone can download the entire database and store it locally. Because Bitcoin uses ECC to secure its transactions, a future quantum computer could, in theory, derive private keys from public ones and reveal which addresses belong to which users. Even if the Bitcoin community migrates to quantum-safe cryptography in the coming years, the study says, transactions that have already occurred would remain vulnerable.
That means hackers could already be gathering the entire blockchain today — harvesting it — and use a quantum computer later to decrypt private data such as digital signatures and wallet ownership. The authors describe this as a “present and ongoing” privacy threat that cannot be fully mitigated after the fact. While future upgrades to post-quantum cryptography may protect new transactions, the data already stored on the blockchain could eventually be read in plain text.
Privacy May be Lost Forever
The Federal Reserve paper explains that the immutability of distributed ledgers, a feature celebrated for enhancing trust, is also their greatest weakness against quantum threats. Because blockchains are designed to preserve every transaction permanently, they inadvertently preserve every vulnerability as well. Once data is encrypted with traditional algorithms and committed to a ledger, it cannot be retroactively re-encrypted without rewriting history. The report emphasizes that even a full network upgrade would not erase past exposures.
The analysts invoke a concept known as Mosca’s Theorem, which measures whether data can remain private before it becomes decryptable. It states that the time it takes to migrate to post-quantum cryptography plus the time the data must stay confidential must be shorter than the time it will take to build a quantum computer capable of breaking it.
For blockchains like Bitcoin, whose records are intended to last indefinitely, that equation offers no real solution. So what’s at stake, then?
A future quantum computer could expose the identities behind pseudonymous Bitcoin addresses, allowing observers to trace payment flows across years and link them to real-world individuals or companies. Dormant or “lost” wallets could be unlocked, smart contract terms and private business logic could be read in plain text, and historical transactions could be cross-referenced with other databases to reconstruct entire financial networks.
In effect, what was once marketed as a privacy-preserving system could become a transparent, searchable archive of global digital finance.
Post-Quantum Fix Limits
Post-quantum cryptography (PQC) refers to new mathematical algorithms designed to withstand attacks from quantum computers. The U.S. National Institute of Standards and Technology has already standardized several of these methods and directed federal agencies to begin migration by 2035, according to the report. The analysts add that the Federal Reserve report supports these efforts but warns that PQC cannot address the HNDL problem for existing data. The paper finds that once encrypted information is publicly available, as in Bitcoin’s ledger, no future algorithm can retroactively hide it.
The study outlines possible responses but concludes that each has severe limits.
Creating a new, quantum-resistant version of the blockchain — a process known as a hard fork — could secure future transactions but would not protect old ones. Mandating the use of PQC-compatible addresses across all wallets and exchanges would reduce exposure going forward but could not enforce universal compliance in a decentralized network.
Even perfect user practices, such as never reusing addresses, cannot prevent harvested historical data from being decrypted later.
Exposure is Inevitable
While the Bitcoin example dominates the study, the same logic applies to any encrypted data that adversaries can collect now, from government communications to medical records. The report notes that large institutions, corporations, and even nation-states may already be stockpiling sensitive information for future quantum decryption. Because migration to PQC is slow and expensive, much of today’s data could remain readable to tomorrow’s quantum systems.
The researchers estimate that the risk period began as early as 1994, when Shor’s algorithm was first published, and will continue indefinitely until classical encryption is phased out. They describe HNDL not as a speculative future hazard but as a standing privacy deficit in the global digital economy. Every day that legacy encryption remains in use, new data joins the pool of information that could one day be revealed.
The Federal Reserve study distinguishes between the integrity and privacy aspects of quantum threats. Much discussion of post-quantum risk focuses on protecting systems from theft or tampering, such as a quantum attack that could forge digital signatures or alter blockchain entries.
But the authors argue that privacy may prove the more intractable issue. Once private keys or encrypted messages are revealed, the confidentiality of past transactions cannot be restored. They note that current discussions of “crypto-agility,” or the ability to update encryption methods quickly, still fail to address this backward-looking risk.
The Need For Transition
The report stops short of prescribing specific solutions but underscores the urgency of preparing for a world where quantum computers are part of the threat landscape. It recommends prioritizing the transition of the most vulnerable encryption systems, especially those protecting long-lived data. The authors describe the development of PQC standards by NIST as essential progress but warn that timeframes for deployment must account for the years it can take to redesign and implement cryptographic infrastructure.
For distributed ledgers, the transition may be even harder. Decentralized governance, cultural resistance to mandatory upgrades, and the global scope of blockchain networks make uniform adoption unlikely. Even if the technical tools become available, coordination across millions of independent users remains a challenge. The result, the study suggests, may be an uneven landscape where only parts of the network are quantum-resistant, leaving older data exposed.
The report concludes that the harvest-now-decrypt-later threat is an unavoidable consequence of how data is currently stored and shared. While post-quantum cryptography will likely protect new transactions and communications, no known method can guarantee the privacy of data already encrypted under vulnerable schemes. For the world’s distributed ledgers — and possibly for much of the internet — the countdown to decryption has already begun.
The analysts write: “We believe the Bitcoin community to be knowledgeable about these risks, capable of weighing the costs and benefits of a forking to achieve crypto agility, coming to consensus on a long-term action plan, and continuously upgrading the network’s cryptographic protections. The difficult question to answer is the extent of adoption by a diverse community of Bitcoin users, with highly varied goals and requirements, and the resulting PQC protections for the network.”
About The Quantum Insider
The Quantum Insider is recognized as the world’s leading source for timely quantum computing news, industry insights, and market intelligence. Our editorial team delivers trusted analysis to researchers, investors, and industry leaders.