Insider Brief
- The European Union has called on member states to transition to quantum-safe encryption by 2030, citing urgent cybersecurity risks posed by future quantum computers.
- The EU plan promotes Post-Quantum Cryptography (PQC) for most sectors and explores Quantum Key Distribution (QKD) for high-security applications, outlining a phased roadmap that begins in 2026 with risk assessments and awareness campaigns.
- Technical and logistical challenges—including limited QKD range, integration issues, and lack of standards—underscore the need for coordinated action among governments, industry, and researchers.
The quickly emerging quantum technology space is causing policymakers to take notice — note recent coverage of Canada and U.S. — and are driving action to mitigate potential hazards of the potentially transformative technology.
The European Union urged its member states last week to adopt quantum-safe encryption methods by the end of the decade, warning that current encryption standards could soon be outdated in the face of rapid advances in quantum computing.
The EU’s call, outlined in a strategic plan from the Network and Information Security (NIS) cooperation group, sets a timeline for transitioning critical sectors such as energy and telecommunications to Post-Quantum Cryptography (PQC) by 2030. According to The Munich Eye, member countries are expected to begin this migration by the end of 2026, with a focus on building national readiness through awareness campaigns, risk assessments, and supply chain resilience.

The push comes amid growing concern about the long-term viability of conventional encryption techniques. Current security protocols rely on complex mathematical problems — such as factoring large numbers — that would take today’s classical computers thousands of years to solve. But quantum computers could potentially crack these systems in a fraction of the time, opening the door to what cybersecurity experts refer to as “store now, decrypt later” attacks. In these attacks, hackers collect encrypted data today with the intention of breaking the encryption once quantum technology matures.
Germany’s Federal Office for Information Security (BSI) estimates that conventional encryption could remain secure for another 10 to 20 years in the absence of sudden breakthroughs, The Munich Eye reports. Europol has echoed that forecast, suggesting a 15-year window before current systems might be compromised. While the timeline is uncertain, European authorities agree that proactive planning is essential.
PQC is designed to resist attacks from both classical and quantum computers by using algorithms based on different kinds of hard mathematical problems. These newer algorithms are more complex and require different computational strategies than those used in today’s standards like RSA and ECC. The EU plan emphasizes the need for what it calls “cryptographic agility”—the ability to switch encryption algorithms as threats evolve and standards mature.
According to The Munich Eye, the NIS group has laid out a multi-phase roadmap that begins with risk analysis and education campaigns, moves toward certification programs and pilot projects, and ultimately aims to establish interchangeable encryption systems. These systems would allow institutions to adapt more easily as new cryptographic techniques are developed and vetted.
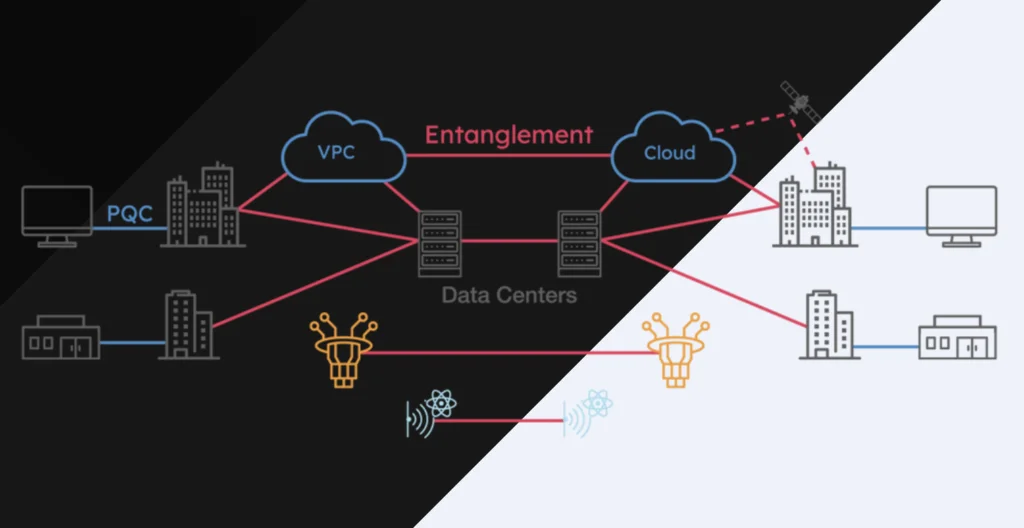
Germany’s VDE, a major electrical engineering and IT association, is advocating for Quantum Key Distribution (QKD), according to the newspaper. Unlike PQC, which uses mathematical algorithms, QKD takes advantage of the laws of quantum physics to allow two parties to share secret keys securely. The approach has attracted interest in sectors with high security demands, such as finance and government.
According to The Munich Eye, research from the Fraunhofer Institute for System and Innovation Research suggests QKD could offer long-term security benefits across critical industries. But despite its promise, QKD remains limited by several technical and logistical challenges.
One of the main issues is distance. Fiber-based QKD is currently limited to around 100 kilometers, and while this can be extended using “trusted nodes” to relay the signal, doing so can introduce new security weaknesses. Researchers are working on developing quantum repeaters to stretch the range without compromising security, but such devices are not yet widely available.
Other hurdles include system stability, integration with existing IT networks, vulnerability to physical attacks, and high deployment costs. Moreover, the lack of standardized, certified QKD systems has slowed adoption. Addressing these issues will require coordinated efforts among European governments, industry players and academic researchers.