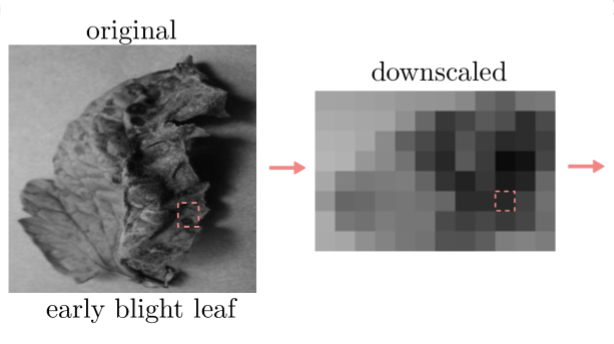
As the concerns with new types of cyber hacks are on the rise due in part to the recent U.S. ransomware hacks, many technology companies are looking for ways to make data more secure. One direction that many companies are taking for increasing security is to use the laws of quantum physics to make a new type of quantum technology that is almost unhackable. This type of research is called “quantum cryptography,” and it uses quantum mechanics to make data more secure. Besides having higher security, quantum cryptography boasts of being able to keep data more secure for longer periods of time, even up to 100 years for electronic data like medical records. Many quantum cryptography systems use photons as the data that is passed between two parties.
The reason quantum cryptography works so well is due to the simple quantum mechanical principle that copying any photons in the encryption message leads to automatic detection. Like many spy movies or detective novels, you typically need a “key” to decode the encrypted message. One of the most widely used key cryptosystems is RSA, used by banks and online shops. RSA, made up of the initials of the three inventors who developed the system, is something that can be improved on with the quantum computer.
One of the most well-known forms of quantum cryptography is Quantum Key Distribution (QKD). A simplified version of QKD works when two QKD machines are connected to an optical fiber and then distribute keys between two parties to read encoded messages. These keys are very special because they use entangled photons. Entanglement is a property of quantum mechanics where two individual photons have connected quantum states, where their quantum states cannot be independent of each other. This means that the photons within the QKD key are inherently connected. For security’s sake, this is a benefit, as anyone trying to intercept, distribute, or read the key that is from an outside source will cause a disturbance in the entanglement, causing the key to shift or become damaged. The two parties involved in the encryption can then communicate a new key between each other, after being immediately alerted of a potential hack.
Many companies are utilizing QKD to develop more secure data centers for networks to use. One such company is ID Quantique, which has been researching quantum cryptography for over 20 years and is based in Geneva, Switzerland. Pejman Panahi, an employee of ID Quantique, explained the need for more quantum cryptography systems in place: “the majority of current encryption methods used in online business, including online shops, are based on principles of public-key exchanges and RSA. The current RSA 2048 bits key which is used by most companies and is considered unbreakable will be broken with quantum computers. Therefore, performing secure online shopping using quantum-safe technologies is a must.” Some corporations are already taking up this call to action, such as Quantum Xchange. They have been able to connect many financial firms in New York City with their data centers in New Jersey. Then, having rented space in existing fiber-optic networks, Quantum Xchange uses its own QKD transmitters and receivers to exchange sensitive information for its clients. Quantum Xchange plans to expand to other urban areas such as Washington D.C. soon.
This shift in securing U.S. fiber-optic networks has become more important in the wake of other country’s efforts, specifically China. In 2016, China launched its first quantum satellite, Micius. This satellite uses QKD-type technology to ensure hack-proof messages. The U.S. has yet to develop or launch a similar satellite. In fact, according to an article from the Brookings Institution, a nonprofit public policy organization, the U.S. may be falling behind in China’s efforts within the development of quantum technology. According to this article, “companies based in China dominate applications for patents in quantum cryptography in the most recent period when data is available, from 2012 to 2016.” It is anyone’s guess as to whether the U.S. will develop similar quantum cryptography satellites, or go in a different direction to make data more secure.

But there are many researchers who are looking past the development of quantum satellites to develop security that is hack-proof, even against a quantum computer. Called post-quantum cryptography, this research assumes quantum computers are accessible enough to be used to hack into other computers. “The current cryptographic tools will have to evolve to address the threat of the quantum computer,” Panahi said. “Several algorithms will have to be replaced by so-called quantum-resistant algorithms. In an interesting twist, quantum technologies will provide new solutions. Quantum Random Number Generators (QRNGs) will help improve all types of cryptographic processes. Quantum Key Distribution (QKD) will help companies and organizations including the healthcare industry to protect themselves against quantum computer attacks, especially for data with long term value.”
In 2016, the National Institute of Standards and Technology (NIST) raised a call to action for corporations to develop potential post-quantum algorithms. In 2019, NIST announced that from the original 69 applications, it whittled down to 26 candidates for helping to develop standards for these quantum-resistant algorithms. It plans to release these standards in 2022.
As our understanding of quantum mechanics advances, so too will our technology. Perhaps our future internet will come with levels of new types of security. We may even have QKD machines for the majority of the population. No matter what happens, quantum cryptography teaches us a valuable lesson: you can never be too careful about securing your data.
**Since the fall of 2019, Quantum Xchange changed their business model and now sells Phio TX — a quantum-safe key distribution system that supports all forms of quantum keys (OKD, PQC, QRNG or a combination) across any network media and any distance to multiple transmission points.
References:
Bushwick, Sophie. “New Encryption System Protects Data from Quantum Computers.” Scientific American. October 8, 2019.
Cardinal, David. “Quantum Cryptography Demystified: How It Works in Plain Language – ExtremeTech.” ExtremeTech. March 11, 2019.
Korolov, Maria. “What Is Quantum Cryptography? It’s No Silver Bullet, but Could Improve Security.” CSO Online. March 12, 2019.
“Quantum Cryptography, Explained | QuantumXC.” Quantumxc.com. 2013.
“Quantum Key Distribution | QKD | Quantum Cryptography.” ID Quantique. 2021
“Sectigo.” Sectigo.com. 2021
Stefanick, Tom. “The State of U.S.-China Quantum Data Security Competition.” Brookings. September 18, 2020.
Wikipedia Contributors. “Quantum Cryptography.” Wikipedia. Wikimedia Foundation. March 21, 2019.
Wikipedia Contributors. “Quantum Key Distribution.” Wikipedia. Wikimedia Foundation. January 9, 2019.
Interviews:
Pejman Panahi of ID Quantique
If you found this article to be informative, you can explore more current quantum news here, exclusives, interviews, and podcasts.